Past two days (after I deciding to use the less stringent on Japanese hosts hostiles), found a handful of Japanese Browse-BOTs that browsed me as soon as I connected to the network (all within 5-10 seconds.) These ones browse repeatedly over a period of time. Here's an example of one today over a 70 minute period:
ID: 59.147.135.13:50652-Tokyo So-net Entertainment Corporation. <- (List, name & shame!)
Code:
8:20:11 AM
8:20:14 AM
8:20:24 AM
8:21:12 AM
8:21:52 AM
8:22:01 AM
8:22:56 AM
8:23:14 AM
8:23:39 AM
8:24:13 AM
8:25:47 AM
8:26:05 AM
8:26:22 AM
8:26:25 AM
8:27:11 AM
8:27:13 AM
8:27:13 AM
8:29:14 AM
8:29:30 AM
8:29:31 AM
8:29:33 AM
8:30:12 AM
8:31:58 AM
8:32:17 AM
8:32:19 AM
8:32:20 AM
8:33:21 AM
8:33:37 AM
8:34:23 AM
8:35:32 AM
8:36:01 AM
8:36:42 AM
8:37:43 AM
8:37:49 AM
8:38:08 AM
8:38:18 AM
8:38:32 AM
8:38:41 AM
8:38:45 AM
8:39:39 AM
8:39:50 AM
8:39:57 AM
8:40:32 AM
8:40:49 AM
8:43:22 AM
8:43:31 AM
8:43:35 AM
8:43:35 AM
8:43:41 AM
8:43:49 AM
8:43:55 AM
8:43:58 AM
8:44:33 AM
8:45:03 AM
8:46:05 AM
8:46:22 AM
8:46:49 AM
8:46:57 AM
8:47:11 AM
8:47:12 AM
8:47:27 AM
8:47:56 AM
8:49:45 AM
8:50:57 AM
8:52:40 AM
8:52:45 AM
8:52:45 AM
8:53:50 AM
8:55:46 AM
8:56:01 AM
8:56:26 AM
8:56:55 AM
8:57:16 AM
8:57:27 AM
8:57:44 AM
8:58:40 AM
8:59:10 AM
8:59:56 AM
9:00:12 AM
9:00:16 AM
9:00:22 AM
9:01:54 AM
9:01:57 AM
9:02:47 AM
9:04:02 AM
9:04:25 AM
9:05:03 AM
9:05:08 AM
9:05:31 AM
9:06:14 AM
9:06:40 AM
9:06:40 AM
9:08:15 AM
9:09:10 AM
9:09:44 AM
9:09:54 AM
9:10:01 AM
9:10:24 AM
9:12:08 AM
9:12:14 AM
9:12:19 AM
9:12:37 AM
9:12:44 AM
9:12:49 AM
9:12:51 AM
9:13:00 AM
9:13:12 AM
9:13:50 AM
9:14:19 AM
9:14:20 AM
9:14:32 AM
9:15:40 AM
9:15:42 AM
9:15:51 AM
9:15:55 AM
9:16:33 AM
9:16:53 AM
9:17:08 AM
9:17:17 AM
9:18:09 AM
9:18:46 AM
9:18:54 AM
9:19:42 AM
9:19:59 AM
9:20:25 AM
9:20:46 AM
9:21:09 AM
9:21:12 AM
9:21:32 AM
9:21:51 AM
You'll notice where I was attempted to be browsed up to 7 and 8 times over a minute. Even after banning the host. I am obviously not the only host this BOT is attempting to constantly browse. Also this is not the only browse-BOT. So if you can imagine several hundred of these browse-BOTs, it starts to become a semi-DDoS.
LW 4 usually shows each occasion a person is browsed. LW 5 / LPE do not. If the Browse listing is still up in the upload window, it will not repeat itself even if you have been browsed several times over a period of time. Only if you clear it from the Upload window will it re-list itself.
The example above was of a new BOT I found today. I checked my firewall log via console & realised the others I found yesterday had also been attempting to browse at a similar rate. Again, up to 8 times a particular minute. Over a period of time the others with slightly greater occurrences than the new BOT today.
Japan BOTs are notorious for deliberately causing heavy traffic. But from my experience, Taiwan BOT's seem to be designed purely for DDoS purposes. ie: not attempting to connect, browse, or download. Simply pinging the program (the firewall console verifies this, example: Allow LimeWire connecting from 1.*.*.*:51768 to port *****)
My answer for helping to prevent the actual program from being pinged into lagginess & eventual crashing is to block various known ip pingers in the firewall. Particularly the Taiwan DDoS BOTs. MS Windows 7 & higher, and some 3rd party firewalls have the ability to block ip's. MacOSX can only achieve it via using 3rd party apps. Personally I use WaterRoof which adds abilities to the OSX built-in firewall, but this app is slow & tedious to add ip's one by one, especially if there's a large list already there. This app should have ability to add a block of ip's at once like Windows firewall does. (1-2 mins between each addition when a large list already exists. Not a well thought out design.)
So you wonder, why is it these Japanese BOTs are browsing everyone & why once is not enough? And why certain BOTs from other parts of the world browse everyone as soon as they can after you first connect to the network?
Edit:
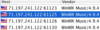
connected to my Phex on 11 May 2014. I added this Washington address to the hostiles 16 March 2013, stated reason was DDoS @ LW & BearShare. I noted it again 19 April for same reason.