
 |
| |||||||
| Register | FAQ | The Twelve Commandments | Members List | Calendar | Arcade | Find the Best VPN | Today's Posts | Search |
| BearShare Open Discussion Open topic discussion for BearShare users
Preview this popular software (BearShare Beta v5 "Download") |
 |
| | LinkBack | Thread Tools | Display Modes |
| ||||
| If anybody is interested ... I think I might have discovered a new network set-up to spam and DDoS based in France. All the host addresses are within two small adjoining sub-ranges of each other. I have not seen any of these host addresses on any other blocklist. Something to keep in mind is some hosts do not attack the client program directly, but once they know your address they will periodically DDoS you. The affect of this a is drop in search results, possible loss of upload and download connections or loss in speed or consistency in either activity, and possible loss of connections with hosts, and at worst loss of internet connection. Those are their purposes. That is why I do strongly recommend blocking the worst of them via your firewall at least. And also to take the weight off your program taking all the hits when they are directed at it but not actually attempting to download or anything (ie: DDoS'ing your program client.) If anybody wants a list of the worst DDoS hosts then just ask. Anyway update to the blocklist will be coming soon. For LimeWire users, I have figured a way for both LW 4 and LW 5 versions to read a blocklist file in similar fashion to BearShare and FrostWire. Except these blocklists for LW use CIDR format which I was told start of year is more memory friendly than the older format BearShare uses. Also, the size of the Heavy/Strong Blocklist is 25% smaller than the original BearShare Blocklist and 10% smaller than the FrostWire blocklist. But is no less powerful. I will post a release on this in a few days time. Still doing last updates to the blocklist which is a very slow process when I have several lists to update.  The LW blocklist version has been tested with 4.14 to 5.6.2. I have not yet tested earlier versions. Results have been seconded by a second person. The LW blocklist version has been tested with 4.14 to 5.6.2. I have not yet tested earlier versions. Results have been seconded by a second person.If you want me to test earlier versions of LW then bump the 'like' this post/thread and give your reason for testing earlier LW versions and it will be done.  |
| |||
| Hi LOTR You, like I, probably suspect that these attacks are sponsored by the RIAA and with tacit approval of of the US Government, even though what is being done to your computer is illegal in most western countries. Plus, while you as an Australian citizen are likely to enjoy the protection of your government, and the sanctity of your laws, in the UK I would have no such protection if I continued to use P2P software. Therefore, while you can continue to use P2P software, because you have broken no Australian law, while I, if accused by the US of doing something against one of their laws, the UK government would virtually say "come and get him, he is all yours". Now, you could call me paranoid because there is nothing tangible I can point to in order to support my position. However, there is enough experiential observations to show that unless a poor unfortunate UK citizen has public support the maxim seems to be "What the US wants the US gets". While you could go to the authorities and complain that your computer is under attack, if I was in your position I would be laughed out of the police station, i.e. if you are hacked or electronically attacked in the UK you can only report it to the police. The way I see things going is that sooner or later the last bastion of individual freedom (Australia) will be sold out to the US, just like the UK has, and there will be concerted pressure to discourage the use of P2P apps, just as it now is in the UK. So, because of the various things happening to discouraged P2P usage, e.g your ISP, various UK government backed campaigns, possible US sanctioned attacks, etc. I no longer use P2P software and the reason why I would not advise anyone else to use it either. UK (Paranoid) Bob |
| ||||
| Quote:
 |
| ||||
| In the March 13 update over half of the new listings are the port 27016 spam clients. So that will take 128 away from the chance to spam you. Others added were spam hosts, DDoS and BOT browsers (ie: 2 kinds; (a) browse you as soon as and every time you log onto the network, (b) browse you robotically every 10-15 minutes. One of these browsed me 5 times over 20 minutes. I was only sharing 500 files which is a fraction of my usual shares.) Don't forget there is also an installer which caters for both BearShare 5.1 beta and other BearShares and choice of which hostiles to install. If anybody wishes to volunteer their services for taking on the updating of the Hostiles, I would love to hear from you. I do not know if there is another equivalent hosted elsewhere that is being updated. AW's old one had not been updated since June 2011 or earlier. As it is, since the LW users do not seem that interested in their updates, I will probably be slowing down my updates for that package or stopping altogether since their 4 lists take considerable time to update. Not many download the updates. But their situation is different. They can ban hosts manually. Whereas BearShare has no other protection choice other than the Hostiles being loaded as it opens. So I do feel as though there is a demand for the BS Hostiles. Received UDP OOB Hits Announcement for GUID: PSXHDKDY(edit) to proxy to Leaf in 7*.1**.*.*** ("BearShare Lite 5.2.0.1" WinXP 2904 msgs) from 188.142.66.5:27016, but the query is stopped. - I wonder what that means? Too much spam being transmitted by Mr. 188.142.66.5:27016 ?  |
| ||||
| I have not heard from the Phex dev for a very long time So I am making my own call here. If you see any Phex version Phex 3.2.0.102 then boot it off your connection list. I have seen far too many of these over very recent past. Absolutely no reason for anybody to be using such an old Phex version below 3.4, so to see so many of them with identical version reminds me of these: Spam sample 1, . . Spam sample 2, . . Spam sample 3, . . Spam sample 4 Example of these Phex BOTs are listed in post #78 below, scroll down to 195.50.2.185. Another range they use is 192.155.80.0 - 192.155.95.255. When I blocked this in Phex, the block count increases by about 31 per minute. |
| ||||
| Past two days (after I deciding to use the less stringent on Japanese hosts hostiles), found a handful of Japanese Browse-BOTs that browsed me as soon as I connected to the network (all within 5-10 seconds.) These ones browse repeatedly over a period of time. Here's an example of one today over a 70 minute period: ID: 59.147.135.13:50652-Tokyo So-net Entertainment Corporation. <- (List, name & shame!) Code: 8:20:11 AM 8:20:14 AM 8:20:24 AM 8:21:12 AM 8:21:52 AM 8:22:01 AM 8:22:56 AM 8:23:14 AM 8:23:39 AM 8:24:13 AM 8:25:47 AM 8:26:05 AM 8:26:22 AM 8:26:25 AM 8:27:11 AM 8:27:13 AM 8:27:13 AM 8:29:14 AM 8:29:30 AM 8:29:31 AM 8:29:33 AM 8:30:12 AM 8:31:58 AM 8:32:17 AM 8:32:19 AM 8:32:20 AM 8:33:21 AM 8:33:37 AM 8:34:23 AM 8:35:32 AM 8:36:01 AM 8:36:42 AM 8:37:43 AM 8:37:49 AM 8:38:08 AM 8:38:18 AM 8:38:32 AM 8:38:41 AM 8:38:45 AM 8:39:39 AM 8:39:50 AM 8:39:57 AM 8:40:32 AM 8:40:49 AM 8:43:22 AM 8:43:31 AM 8:43:35 AM 8:43:35 AM 8:43:41 AM 8:43:49 AM 8:43:55 AM 8:43:58 AM 8:44:33 AM 8:45:03 AM 8:46:05 AM 8:46:22 AM 8:46:49 AM 8:46:57 AM 8:47:11 AM 8:47:12 AM 8:47:27 AM 8:47:56 AM 8:49:45 AM 8:50:57 AM 8:52:40 AM 8:52:45 AM 8:52:45 AM 8:53:50 AM 8:55:46 AM 8:56:01 AM 8:56:26 AM 8:56:55 AM 8:57:16 AM 8:57:27 AM 8:57:44 AM 8:58:40 AM 8:59:10 AM 8:59:56 AM 9:00:12 AM 9:00:16 AM 9:00:22 AM 9:01:54 AM 9:01:57 AM 9:02:47 AM 9:04:02 AM 9:04:25 AM 9:05:03 AM 9:05:08 AM 9:05:31 AM 9:06:14 AM 9:06:40 AM 9:06:40 AM 9:08:15 AM 9:09:10 AM 9:09:44 AM 9:09:54 AM 9:10:01 AM 9:10:24 AM 9:12:08 AM 9:12:14 AM 9:12:19 AM 9:12:37 AM 9:12:44 AM 9:12:49 AM 9:12:51 AM 9:13:00 AM 9:13:12 AM 9:13:50 AM 9:14:19 AM 9:14:20 AM 9:14:32 AM 9:15:40 AM 9:15:42 AM 9:15:51 AM 9:15:55 AM 9:16:33 AM 9:16:53 AM 9:17:08 AM 9:17:17 AM 9:18:09 AM 9:18:46 AM 9:18:54 AM 9:19:42 AM 9:19:59 AM 9:20:25 AM 9:20:46 AM 9:21:09 AM 9:21:12 AM 9:21:32 AM 9:21:51 AM LW 4 usually shows each occasion a person is browsed. LW 5 / LPE do not. If the Browse listing is still up in the upload window, it will not repeat itself even if you have been browsed several times over a period of time. Only if you clear it from the Upload window will it re-list itself. The example above was of a new BOT I found today. I checked my firewall log via console & realised the others I found yesterday had also been attempting to browse at a similar rate. Again, up to 8 times a particular minute. Over a period of time the others with slightly greater occurrences than the new BOT today. Japan BOTs are notorious for deliberately causing heavy traffic. But from my experience, Taiwan BOT's seem to be designed purely for DDoS purposes. ie: not attempting to connect, browse, or download. Simply pinging the program (the firewall console verifies this, example: Allow LimeWire connecting from 1.*.*.*:51768 to port *****) My answer for helping to prevent the actual program from being pinged into lagginess & eventual crashing is to block various known ip pingers in the firewall. Particularly the Taiwan DDoS BOTs. MS Windows 7 & higher, and some 3rd party firewalls have the ability to block ip's. MacOSX can only achieve it via using 3rd party apps. Personally I use WaterRoof which adds abilities to the OSX built-in firewall, but this app is slow & tedious to add ip's one by one, especially if there's a large list already there. This app should have ability to add a block of ip's at once like Windows firewall does. (1-2 mins between each addition when a large list already exists. Not a well thought out design.) So you wonder, why is it these Japanese BOTs are browsing everyone & why once is not enough? And why certain BOTs from other parts of the world browse everyone as soon as they can after you first connect to the network? Edit: 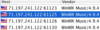 connected to my Phex on 11 May 2014. I added this Washington address to the hostiles 16 March 2013, stated reason was DDoS @ LW & BearShare. I noted it again 19 April for same reason. connected to my Phex on 11 May 2014. I added this Washington address to the hostiles 16 March 2013, stated reason was DDoS @ LW & BearShare. I noted it again 19 April for same reason. |
| ||||
| Just thought I'd give a few simple examples of BOTs on the network from a couple days ago: Code: 50.22.64.163:2870 50.22.64.180:2821 50.22.64.181:2992 50.22.64.186:4716 50.22.64.188:4310 50.22.78.249:2220 50.22.78.250:3919 50.22.78.252:2085 50.22.158.131:4236 50.22.158.146:1517 50.22.158.148:3132 50.22.186.2:3050 50.22.186.3:2926 50.22.186.4:4939 50.22.186.7:2670 50.22.186.9:2684 50.22.186.10:4720 50.22.186.11:2417 50.22.186.19:2960 50.22.186.20:3321 50.22.214.66:3259 50.22.214.71:3200 50.22.214.74:3715 50.22.214.75:4567 50.22.214.85:1657 50.22.214.89:3422 50.23.91.87:4602 50.23.91.88:1227 50.23.112.4:2487 50.23.112.15:4777 50.23.112.19:4827 50.23.112.28:1177 50.23.112.29:2420 50.23.112.35:1059 50.23.112.36:4082 50.23.112.43:1792 50.23.112.44:4268 50.97.156.201:2770 50.97.156.202:2710 50.97.156.203:3498 50.97.156.207:1244 50.97.156.208:4052 50.97.156.209:1282 50.97.156.215:3268 50.97.156.218:1518 50.97.156.220:3442 50.97.156.221:3408 50.97.156.222:4252 66.212.143.98 66.212.143.106:65229 66.212.143.107:62997 66.212.143.110:56262 66.212.143.116:57379 75.126.109.2 75.126.109.8:3581 75.126.109.9:4572 75.126.109.13:4370 75.126.109.14 75.126.109.18:4827 75.126.109.19:2269 75.126.109.20:3956 75.126.109.27:1971 75.126.109.28:4166 75.126.109.29:1899 75.126.109.33:4911 75.126.109.34 75.126.109.35:2969 154.45.216.140:59405 154.45.216.147:40807 154.45.216.148:46792 154.45.216.154:60824 154.45.216.155:43358 154.45.216.158:51433 154.45.216.159:36646 154.45.216.161:50887 154.45.216.162:40197 154.45.216.163:40206 154.45.216.163:40862 154.45.216.165:37093 154.45.216.166:34054 154.45.216.167:38168 154.45.216.169:47042 154.45.216.172:53731 154.45.216.176:58789 154.45.216.178:38092 154.45.216.179:47561 154.45.216.181:38580 154.45.216.182:42042 154.45.216.184:60297 154.45.216.186:55441 154.45.216.189:34107 154.45.216.190:43937 154.45.216.199:50241 159.253.131.136:4502 159.253.131.144:2232 159.253.131.149:4243 159.253.131.155:3025 159.253.131.163:1492 159.253.131.181:3654 159.253.131.187:2720 159.253.131.190:4414 159.253.131.192:3714 159.253.131.201:4914 159.253.131.205:1662 159.253.131.213:1963 159.253.131.217:2718 159.253.131.219:3561 159.253.131.225:4799 159.253.131.230:2304 159.253.131.231:3740 159.253.143.250:1328 159.253.143.251:2920 184.173.143.8:1211 184.173.143.9:4048 184.173.143.10:4477 184.173.143.13:1532 184.173.143.15:2324 184.173.143.23:2182 184.173.143.24:2764 184.173.220.179:2191 184.173.220.182:4297 195.50.2.185:46028 Phex 3.2.0.102 (3/2.0 GB) first 195.50.2.185:46028 Phex 3.2.0.102 (1/4.0 MB) 10-15 mins later 195.50.2.185:14799 Phex 3.2.0.102 (5411/2.0 GB) first 195.50.2.185:14799 Phex 3.2.0.102 (21/128 MB) 40 mins later 195.50.2.185:14799 Phex 3.2.0.102 (40931/16 GB) an hour later * 195.50.2.185:29936 Phex 3.2.0.102 (78/512 MB) first 195.50.2.185:29936 Phex 3.2.0.102 (40/1.0 GB) an hour later 195.50.2.185:38940 Phex 3.2.0.102 (245/2.0 GB) first 195.50.2.185:38940 Phex 3.2.0.102 (40/1.0 GB) an hour later 195.50.2.185:50145 Phex 3.2.0.102 (4/512 MB) _ (All Belarus) 204.51.224.224:51099 204.51.224.225:50987 204.51.224.226:55918 204.51.224.227:52179 204.51.224.228:56571 204.51.224.229:64402 204.51.224.233:49724 204.51.224.236:64302 This example is simply a recent capture of them via the firewall console (with a few exceptions such as the 2007 version Phex ones from March - blood suckers.) |
| ||||
| This snapshot is from 29 June 2016. It shows a mass of LW 4.14 Download-BOTs in the upload window of Phex. LW 4.14 was my favorite LW 4 version (and then 4.16). But there is some doubt these really are LW 4.14 or modified 4.14 versions. It's been known for about a decade that some BOTs can change program ID on the fly. Some of the BOTs have same ip address but different port and some are downloading the exact same file. Amazon ip range; generally a professional proxy service to hide and protect the original business's source. 54.187.25.79 54.187.186.48 54.187.240.221 54.187.246.227 54.191.73.20 54.200.31.26 54.200.95.239 54.201.11.100 All Amazon.com ip ranges. Hostname .us-west-2.compute.amazonaws.com Interestingly just 7 days earlier via a GWC I came across 54.201.11.100:4396 Gnucleus 2.0.9.0 (GnucDNA 1.1.1.4) which is most likely what all of these so-called LW 4.14's are actually using. Same probably applies to the LW 4.12 Download-BOTs discussed elsewhere. |
| ||||
| I'm one of those rare people that keeps an eye on their uploads (& network as a whole.) Last night whilst using WireShare I was surprised to see my upload window full before noticing the pseudo-name SmilingPig beside many of them and with different identifying addresses. One alarm bell was that the host was identifying itself as LimeZilla/1.8 (if it really was LimeZilla), but this version is ancient. LimeZilla is up to using version 4 nowadays. Two of the uploads SmilingPig was downloading/queued to download were the same two files; thus 4 upload/queue slots for two files. Surprised it was not sapping the entire upload bandwidth made available to WireShare however. ISP: NFOrce Entertainment B.V. Netherlands; Netname: Amsterdam_Residential_Television_and_Internet_Netw ork. Services: Network sharing device or proxy server. IP addresses blocked: 212.92.108.24 212.92.108.34 212.92.108.44 212.92.108.84 212.92.108.224 212.92.111.192 212.92.112.81 212.92.112.101 212.92.112.181 212.92.114.178 212.92.115.67 212.92.117.65 212.92.117.155 212.92.119.143 212.92.121.97 212.92.123.116 212.92.124.91 212.92.124.211 212.92.124.221 Upload window: (WireShare's display of total upload bandwidth had not yet caught up at the moment of this snapshot) 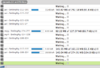 After blocking several, more showed up: 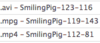 Then another attack a day later with 16 fresh addresses within the same sub-ranges. It also browsed me. 212.92.104.85 212.92.105.147 212.92.108.54 212.92.109.34 212.92.115.77 212.92.115.107 212.92.116.246 212.92.117.75 212.92.118.94 212.92.120.208 212.92.120.218 212.92.121.167 212.92.122.136 212.92.122.206 212.92.123.65 212.92.123.75 If you look carefully among the two lists you will notice the same sub-ranges using the same last number.  Example: all those in the 212.92.115.* range use 7 as the last number, all those in the .108.* range using 4 as the last number, etc. Although the .123.* range shows a variance. Example: all those in the 212.92.115.* range use 7 as the last number, all those in the .108.* range using 4 as the last number, etc. Although the .123.* range shows a variance.Edit 2018-04-29: Discovered this from a GWebCache: 212.92.122.146:50903 (u:23:18:29) 2018-01-04. 212.92.123.162:50903 (u:23:18:05) 2018-01-04. Host using WireShare or identifies itself as WireShare. Not sure this WireShare host could be trusted. Last edited by Lord of the Rings; April 28th, 2018 at 08:38 PM. Reason: Added new finding at bottom of post. |
 |
| |
 LinkBacks (?)
LinkBacks (?)
LinkBack to this Thread: https://www.gnutellaforums.com/bearshare-open-discussion/53973-technutopia-fullsize-hostiles-list-bearshare-limewire.html | ||||
| Posted By | For | Type | Date | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 22nd, 2016 09:01 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 11th, 2014 10:48 AM | |
| Site Gnutella Forums | www.gnutellaforums.com | BoardReader | This thread | Refback | May 7th, 2014 04:33 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | December 18th, 2013 03:15 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | November 5th, 2013 02:07 AM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 03:15 PM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 03:39 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | July 14th, 2013 04:01 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | May 21st, 2013 12:24 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | May 4th, 2013 05:05 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | March 15th, 2013 11:11 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 24th, 2013 05:36 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | November 5th, 2012 12:37 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | October 8th, 2012 09:59 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 7th, 2012 04:05 AM | |
 Similar Threads
Similar Threads | ||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| The TechNutopia Fullsize Hostiles List for BearShare and LimeWire | AaronWalkhouse | Tips & Tricks | 18 | March 20th, 2009 09:45 PM |
| Hostiles File - I'm Lost | ADKR | General Windows Support | 7 | December 25th, 2007 08:03 PM |
| Is anybody having trouble connecting to www.technutopia.com? | AaronWalkhouse | Chat - Open Topics - The Lounge | 19 | August 6th, 2006 06:34 PM |
| The LimeWire Fullsize Hostiles List. | AaronWalkhouse | New Feature Requests | 1 | July 16th, 2005 06:03 PM |
| hostiles.txt in CVS tree | number_man | Gtk-Gnutella (Linux/Unix/Mac OSX/Windows) | 0 | May 22nd, 2004 07:58 AM |