
November 22nd, 2017
|
 | ContraBanned | | Join Date: June 30th, 2004 Location: Middle of the ocean apparently (middle earth)
Posts: 684
| |
An example of BOTs still around the network in 2017. Running BearShare without the hostiles file resulted in a notable number of BOTs connecting. Although I did sew some of these (the 4.12 Pro's) together over about an hour due to them only connecting briefly. Also some of these were downloading from me. Every host shown is a BOT. 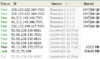
All those hosts are not what they appear to be, they give fake ID's.
Here's a couple of examples from several years ago: seen via Phex and seen via BearShare
The present version of BearShare Hostiles (Jan 2016) is somewhat out of date but will still do a good job of blocking out most BOTs. But unfortunately will also block out a heck of a lot of innocent hosts. Even my own dynamic address has changed to a different blocked range six or so occasions this year (no exaggeration.) I hope I'll be able to release an update over coming weeks or so. |





 Similar Threads
Similar Threads