
 |
| |||||||
| Register | FAQ | The Twelve Commandments | Members List | Calendar | Arcade | Find the Best VPN | Today's Posts | Search |
| BearShare Open Discussion Open topic discussion for BearShare users
Preview this popular software (BearShare Beta v5 "Download") |
 |
| | LinkBack | Thread Tools | Display Modes |
| ||||
| Feel free to put these host addresses on your ban lists. These are hosts set up to DDoS various gnutella clients. 72.22.25.1 - 72.22.25.127 217.239.2.2 216.174.143.145 70.83.206.27 76.114.35.182 80.67.3.14 84.196.11.75 84.196.82.177 70.30.239.145 The first listing is obviously a network of DDoS hosts. Hosts anywhere from 72.22.25.1 to 72.22.25.127 will DDoS your client 1-5 times per second each for hours and days on end. They will mostly do their deeds to those sharing lots of files. It might even be wise to ban the above hosts in your router's firewall settings if your router has that option. If you find your internet browsing is getting slow, you are probably being DDoS'd by these hosts. Your firewall log should tell you if this is happening. Another effect of this DDoS is lack of search results by your gnutella client. The 216.174.143.145 or 216.174.143.0/24 range added up to 10099 pings which equated to about 600/hour or 10 pings/minute. I discovered some clients like LimeWire 5 have an individual ID. So even force-changing ip address made no difference. And deleting the client ID in the settings file seems to make no difference, it may have been set internally upon installation. Though this might not be the reason for the quick rediscovery by the DDoS hosts. For those using LimeWire 5/LPE who wanted to ban such hosts via LW itself, the first would be best banned by using this format: 72.22.25.0/25 which covers half of that sub-range. This is a memory efficient binary process of representing ip host addresses which the later LW 4 versions understood, but I am not sure BearShare understood. But this will not prevent such hosts from at least reaching your client program, so it's best to ban them either at firewall or router level so they are unable to intrude and affect traffic levels and as such your personal web-browsing. ie: stop them even getting passed your router or firewall, your router probably being the best option to prevent their actions and effects. (Edit: adding more) 70.38.38.101 - 70.38.38.217 . . (5 hosts seen in this range heaps of pings, maybe spam) 70.38.54.15 - 70.38.54.244 . . (15 DDoS hosts seen within this range) 75.40.34.169 . . (major DDoS host) 174.131.182.240 . . (major DDoS host) 188.165.220.59 * . . (major DDoS host) - Uses LimeWire 5.1.2 ... not one host, a network of many using different ports. No doubt the MediaDefender company. 188.165.230.147 * . . (major DDoS host) 199.127.249.19 - 199.127.249.247 . . (15 within this range) This and one below are heavy DDOS pingers from NY USA. Coincidentally same address ranges are already in the Full Hostiles list. Firewall is best so the ping hits will not affect LW's performance. 199.127.253.8 - 199.127.253.124 . . (11 within this range) 208.93.7.14 - 208.93.7.254 . . (7 hosts seen in this range, spam) * I discovered via Phex these are not the only host addresses MediaDefender use within these sub-ranges ! Phex's block count for both 188.165.220.0/24 and 188.165.230.0/24 are continually increasing. The specific addresses listed above were already blocked via firewall, thus could not reach Phex. If you are using Phex, you can actually watch as those in the 188.165.220.0/24 and 188.165.230.0/24 are blocked out and starts to add up into dozens and eventually hundreds. That is if you have them blocked at the Phex level and not in the firewall or router already.  Just as a test, I white-listed 188.165.220.59 for a while and sure enough, their colors showed. Example of MediaDefender's clients below: ->  <- (click to see image, click twice to open in its own window) <- (click to see image, click twice to open in its own window)(all LW 5.1.2, all same ip address, simply different ports for each client. Remind you of this?) Edited again to add some more: And some more listings in order of ping frequency grouped into sub-ranges where applicable: 86.11.111.162 173.32.197.229 65.83.131.202 67.205.112.173 98.116.165.20 211.18.159.174 125.30.13.56 115.124.174.213 208.99.193.58 98.195.206.182 70.38.37.22 * (70.38.37.? is a sub-range also widely used, similar to previous 70.38.?.? listings above. Personal choice, but if you block 70.38.38.0/24 and 70.38.54.0/24 in your router-firewall the heavy hits do not affect the internet speed of other computers using the same router. Compared to if you only banned the range in your software firewall on one computer.) 64.6.132.197 and 64.6.132.200 1.171.212.33 98.228.15.122 50.23.112.2 - 50.23.112.25 . . (4 hosts) 69.171.166.13 - 69.171.166.206 . . (4 hosts) 69.171.171.39 - 69.171.172.190 . . (4 hosts) 69.171.163.54 - 69.171.163.152 . . (6 hosts) 66.212.143.105 - 66.212.143.116 . . (5 hosts) 66.212.143.105, 66.212.143.106, 66.212.143.107, 66.212.143.110, 66.212.143.116 - (Multiple hosts per host address, see Dec. 21, 2012 snapshot below) 66.249.5.139 80.6.254.38 58.96.85.205 74.171.214.5 122.135.45.6 207.6.231.91 50.58.238.131 - (this one is always consistently high with pings) 173.193.77.4 - 173.193.77.62 . . (3 hosts) 76.73.128.75 50.18.227.125 50.196.56.94 - Specifically a BeaShare DDoS host. 190.71.233.91 - Specifically a BeaShare DDoS host. 66.56.213.56 - Specifically a BeaShare DDoS host, but is a dynamic address. 66.142.89.210 - Specifically a BeaShare DDoS host, but is a dynamic address. 69.141.48.179 - Specifically a BeaShare DDoS host, but is a dynamic address. 68.98.199.166 - Specifically a BeaShare DDoS host, but is a dynamic address. 68.82.158.29 - Specifically a BeaShare DDoS host, but is a dynamic address. 24.9.10.51 - Specifically a BeaShare DDoS host, but is a dynamic address. 69.171.160.30 and 69.171.160.68 . . (2 hosts) about equal, so arranged numerically: 24.242.233.252 38.101.222.251 65.199.18.0/24 - Various hosts. Known upload slot containers. Also on original hostiles list. 83.211.103.159 88.123.195.66 94.193.183.239 99.251.185.253 123.110.82.95 154.45.216.163 154.45.216.177 154.45.216.185 159.253.131.147 159.253.131.162 159.253.131.213 159.253.131.230 175.98.48.201 180.218.80.193 182.233.240.232 184.173.3.44 - 184.173.3.50 . . (2 hosts) 187.78.164.190 206.45.6.228 218.15.114.134 218.160.153.248 218.187.115.208 218.187.119.80 219.70.10.90 220.140.232.58 220.142.3.66 - 220.142.3.189 . . (2 hosts) May 28, 20013: Using Phex, same upload-slot containers I'd had problems with 12 months earlier. As a test I opened 39 upload slots (Upload.MaxParallelUploads=39) with only one slot per host. Guess what, 39 hosts of all different client program types and more than one of each downloading from me. Almost all had same ip address and port number. They download the largest audio files (in my case, FLAC), largest collection of file-topics, etc. Image is a snapshot of 29 of them put side by side for viewing purposes (this was not all of them.):  And the Phex connection file showed these addresses. (All belong to BMI (Broadcast Music, Inc. )) 66.212.143.104:7001 66.212.143.105:7001 66.212.143.106:7001 66.212.143.107:7001 66.212.143.110:7001 66.212.143.116:7001 Dec. 21, 2012: Here's a funny episode. Whilst using BearShare I accidentally replaced my BearShare hostiles with the original and ... these hosts, each time I removed them they were replaced with more of same ip address or similar, example 3 snaps joined here (all same port, all same shares):  Mid-September 2012 (all connected to me at once - my ip block was off for testing): 199.127.249.95:38790 - LimeSharePro/1.5.0 199.127.249.95:38229 - morph500 199.127.249.241:20433 - WinMX Music 199.127.253.17:36696 - Gtk-Gnutella 199.127.253.17:40695 - WinMX Music 199.127.253.89:36865 - morph500 199.127.253.89:38982 - WinMX Music 199.127.253.89:46032 - WinMX Music China and Hong Kong seemed to have joined with Taiwan to become a major DDoS threat. A quick example from my console log: 15/11/12 12:27:01 PM Firewall[133] Allow LimeWire connecting from 222.93.119.95:2435 (China) 15/11/12 12:31:43 PM Firewall[133] Allow LimeWire connecting from 203.198.79.125:7791 (Hong Kong) Example of one of each from multitudes, and different addresses. But they did not connect, did not upload/download. Just pinging LW for the sake of it. If you wish China and Hong Kong blocks for your firewall I will attach below when I have finished the list. In some ways it would be a smaller list if they were combined with Taiwan and possibly Japan because their ip ranges are often adjoining. Many/most of the asian ip ranges are side by side each other. I was watching BS's console and saw this: "Discarding questionable cache entry http://216.18.206.17:2108/gwc/cgi-bin/fc" I suspect that was a gwc site I tested from an entry from a LW clone cache listing. Though I may have obtained it from another source. It falls within the Hostiles ranges. Firewall blocks: Blocking hostile hosts in the firewall reduces lag and loss of performance of your file-sharing program! You will also get better search results and download and upload performance. Port blocks: * Recommended to block ports 27016 and 7001 in your firewall. These ports are used by companies of spammers only. My firewall block count adds up considerably over time with the 27016 listing. Block these ports for both TCP and UDP. I get about 10 times more blocks with UDP for this port (example over 6,000 blocks of compared to 600 odd of TCP of spam hosts over a period of a day.) Windows 7 and 8 firewall can be set to block specific incoming ports easily using the incoming rules for blocking. MacOSX firewall needs some tricks to block ports or specific hosts. I've come to the conclusion hosts with port 27016 use ip address proxy switchers. Whereas port 7001 hosts seem to be static ip addresses. However, I do have several records of the port 27016 hosts keeping same address (23 April - 19 July 2013 for example, not bad considering it is officially a dynamic USA address, obviously sticky dynamic.) And another good example was 8 May, 29 June & 7 July seen with same Belgian address. And another good example early May to July static USA address. So I'm reviewing my decision to leave dynamic addresses and at some point (a couple months ago), all port 27016 ip addresses off the hostiles. It seems they do either re-use some addresses since they are still available for proxying or simply maintain their use. Other reason of course is different spam groups based in different countries use different approaches with their ip addressing. AFAIK, LW 5 or the later LW 5 versions and LPE have an in-built block for either port 27016 or the LW4.21.1(rc) hosts. Strange FrostWire did not follow suit because FW4 (& all the LW4 clones) has a severe problem with such spam hosts. Phex has a user option for port blocking. I added certain port blocks via the connection-fix for Phex which also has other off-topic benefits. BearShare totally relies on the Hostiles. Which is why I recommend firewall blocking to assist. Edit September 2013: I noticed from a 2009 BetterShare connection file a common spam port seemed to be 41000. Not sure that port is still being used. It does not show up on any of my gnutella program connection lists or spam log file. I think port 41000 can be ignored for now. Sample image showing how to block port 27016 in Windows 7 Firewall for TCP. Same should be done for UDP also. Windows 7 Port block sample image and Sample 2. Specific details how to do it are here. * Sorry, last year I gave incorrect instructions, this one is correct.  (Nobody told me.) (Nobody told me.)How to set up a port block rule when you are port forwarding your router? This applies for Windows 7 or later. Set up a rule based on port. For example, block port 27016. Then double click the rule after saving so the rule is open for editing. Choose Programs and Services tab. Then check option for 'This Program'. Browse to find the program, example BearShare. Save and click OK. Alternatively set up a custom rule with same settings as suggested: Select port and then program and block. The rule has now become a specific port block rule only applying to that specific program. Otherwise port forwarding the program may by-pass any specific port block rule. A separate rule should be done for each of both TCP and UDP. Wise to also block port 7001 in same fashion. 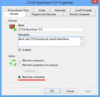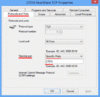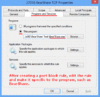 How to add an ip block list to Kaspersky Firewall. 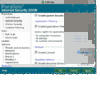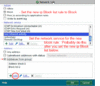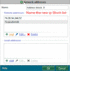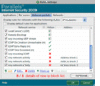 Firewall -> Settings -> Network Packets -> select 'Addresses from Group' and click Add -> click Add to add an ip address and continue doing this. After adding all the addresses, name the rule something like 'ip address block list' & click OK. Make sure that rule is still selected in the Network Packets section and select 'Block' at top and 'Any Network Activity' in the middle section. Though you can select the Block option after selecting addresses from group option near beginning of the process. A Gnutella ip Group Block in Windows 7 and 8 Firewall Windows 7 and 8's firewall have the option for doing a group block. I created one for TCP and UDP. In fact, you only need to do one then duplicate it and change the rule's protocol from TCP to UDP then rename it or a single group rule and set the protocol to All. Sounds easy?  Set up a new inbound rule, and set it to Custom. Choose either all programs or LimeWire/FrostWire/BearShare, etc. path, then all ports. Then start adding the host addresses you wish to add. Then when finished, name the rule. I have created a sample image but note, the sample GiF is a little large in size and has quite a few frames. The advantage of a group block is you could disable it if or when necessary, or simply set it to only apply for LimeWire/FrostWire/BearShare, etc. in the program/path option. Set up a new inbound rule, and set it to Custom. Choose either all programs or LimeWire/FrostWire/BearShare, etc. path, then all ports. Then start adding the host addresses you wish to add. Then when finished, name the rule. I have created a sample image but note, the sample GiF is a little large in size and has quite a few frames. The advantage of a group block is you could disable it if or when necessary, or simply set it to only apply for LimeWire/FrostWire/BearShare, etc. in the program/path option.Windows 7 firewall ip Group block (sample image). And Second sample (this sample only needs a single rule by using the 'Any' protocol and applied specifically to the program to be used for.) Blocking hostile hosts in the firewall reduces lag and loss of performance of your file-sharing program. Outgoing rules? Why set up outgoing rules to block certain ip ranges instead of only incoming rule blocks? Because if you are sharing files, your program sends your shared files details that correspond to a particular search. Do hostile clients search? Since some hostile clients are known to browse hosts, then chances are they also do searches. Hosts with port - 7001 are known as upload-slot containers, they will download everything you have, they get paid to do this to prevent you sharing to anybody else. Having equivalent outgoing rules may help to slightly reduce some incoming traffic from bad hosts. Example: deny ip from me to 50.58.238.131 . (resulting packets over 50 minutes = 1338 and after 270 mins = 7734; Starting up as a UP, after 50 mins = 2144) - (consistent climber of stats every minute or two 24 hrs/day) deny ip from 50.58.238.131 to me . (resulting packets over 50 minutes = 0 and after 270 mins = 3; Starting up as a UP, after 50 mins = 104) (the outgoing rule listed first!) The attachment below is the binary system used by LimeWire for ip address blocking and 'some' firewalls for banning ip addresses. ie: 256 possible addresses for each block/sub-range x.x.x.x thus, 2 to the power 32 = 2^32 = 256x256x256x256=4,294,967,296 In the Kaspersky Firewall example above, you will see I chose 72.22.25.0/25 which represents a range from 72.22.25.0 to 72.22.25.127 which is half a sub-range. Or 72.22.25.128/25 would be 72.22.25.128 to 72.22.25.255. 72.22.25.0/24 would have been a full sub-range from 72.22.25.0 to 72.22.25.255. Whereas /32 represents a single ip address, /31 = 2 sequential addresses, /30 = 4 sequential addresses, /29 represents 8 sequential ip addresses, etc., doubling with each step. I like to see the sub-ranges as A.B.C.D representing x.x.x.x for ease of reference. Thus my text example attachment below-bottom. Nobody is pretending this is easy to learn, at first seems rather difficult. That's why I set up a reference list for myself so there would be less chance of errors. . . . This also helps give some picture of how it works. Last edited by Lord of the Rings; May 28th, 2013 at 09:08 AM. Reason: Re-did port block sample for Windows 7, since my original was incorrect. Added Phex spam sample |
| ||||
| For any LimeWire users who wished to block out Japan and Taiwan hosts, see http://www.gnutellaforums.com/limewi...tml#post369081 Some other clients such as Phex and GTK-Gnutella could also use this list with the notation it uses. However, I do not think BearShare 5 was set up to use that kind of ip address notation format. I do not understand the older notation BearShare used, but I could investigate to try to learn how it works. |
| |||
| BearShare use the Hostiles.txt to handle ip adresses which it should not connect to and block them out from the search results, thats the only way for BearShare to use a block list like that...
__________________ Just Good enough, smart enough, and no longer Elite...  |
| ||||
| I have updated the Fullsize Hostiles block list file after figuring out how to do it.  This list not only adds new listings of spam networks and known spam addresses, but also adds Japan and Taiwan to the list. In effect, because some of the ranges removed many thousands of previous individual listings, the overall size of the block list is now 10% smaller than the previous block list last updated over a year ago. This should make it a little faster to load when opening BearShare and use a fraction less RAM memory. The size of this list is about 54,000 less listings and about 2 MB smaller than the previous hostiles list file. However, no previous hosts have been removed from the list, they are still within the ban ranges for better or worse. I did not think I was the appropriate person to choose what to remove. If you wish to download Japanese related material, then choose the BearShare - Hostiles Blocklist 2012-NoJapBlocks.zip version. The reasons for the addition of Taiwan and Japan are (1) their large numbers with spamming and other kinds of anti-file-sharing activities, such as deliberate upload slot containment and robotic browsing, and heavily pinging users. (2) to assist people's searches to return more culturally similar results. This is also assisted when you are not connected directly to several such hosts. The list may be updated on the fly without notice. And is likely to be updated at least monthly or bi-monthly. (Edit: hostiles is updated approximately every 2 months.) The links? Oh the links: Download the Fullsize Hostiles List 2013 via MediaFire . or via SaberCat or Download the Fullsize Hostiles List 2013 via 4Shared (need to be a 4Shared member to use their downloads) and the no Jap Block version via 4Shared. If you would prefer an installer for the Fullsize Blocklist, then see either the Hotfile or filecloud links. Edit February 2013: a single installer is now inclusive of both options and for either standard BearShare or the BearShare 5.1 Beta Test version. (Also removed uninstall data from all installers. I previously had no idea this had been included by default without anything in the code to say it had been.) Edit March: fixed a small silly error I made with the installer. Apologies if it affected anyone who downloaded the February installer as one choice would not install an appropriate file.  The hostiles files have been put together in same folder as other BearShare material to download from (with exception of the 4Shared links.) This makes it easier to update the files without changing the forum's download links. Windows 8 users will either need to use the installer or else, change the permissions of the BearShare program folder and reboot computer so you have permission to replace items in the db folder. BTW as a note, if you read the first page of this thread, someone was put on the hostiles list for simply having 2 files in their shares which coincidentally matched the same size as a common spam file of that time. This suggests there are probably other listings of similar nature. I noticed that person's address was not removed from the hostiles list and in fact the entire sub-range and next one to it are banned. I presume there was a valid reason for this such as multiple findings in each of those small sub-ranges. The average true spammer has a lot more than two spam files in their shares, if you have ever browsed one you will know what I mean. Mind you, those posts on the first page were from over 5 years ago. But I doubt a hash check of the files was done at the time to verify they were spam files. (The asian blocklist is not intended to be any kind of insult to the asian community. This block incorporation is due to sensible file-sharing. And due to forum members noting their frustrations to only or mostly connecting to asian hosts. As a personal note, personally, I studied 3 asian languages at university, and unofficially other asian languages and many dialects including Japanese dialects. I have a high appreciation of Japanese culture. I have spent months at a time traveling asia. Not to mention our work and friendships alongside. And several years sharing accommodation locally. ie: the blocklist is due to 'underhand' RIAA, and similar sponsored group pressure. Don't we love Sony's music and video/film company interests ... cough coff!!! They destroyed our local music industry, that's enough for me! They walked in bought up all the local music companies, sacked so many successful local bands, then americanised the local music industry all so commercially .. yew! pewk! Australia's music has no independent styles now, .. it simply copies what the usa music companies want them to. pfft .. I'm more than happy to protect my ears from that crap lol .. sorry, as usual starting to ... but anyway, americanisation of music means variant styles and independency and originality of musical ideas vaporise. And people once asked, whatever happened to the great designers of new ideas and products and concepts that came from our country throughout our entire history that we were secretly famous for, why not now?) Last edited by Lord of the Rings; December 6th, 2013 at 11:57 PM. Reason: Replaced HotFire links with MediaFire |
| ||||
| I was just looking at my firewall ip pings. Realised one specific ip I had put there has over 5,000 pings. I cannot remember why I put it there lol. I'm guessing it was a finding I forgot to report here (luckily it's a static address as are all in that range.) This ip is not in the Hostiles list, but will be in the next updated version. This amount of pings is about the fifth most I'm getting but the others are ip ranges. Most is the infamous 70.38. range with 31,000. Taiwan and Japan next with over 7,000 in specific ranges each. For LimeWire 5 users, I will put out an experimental shortened version of the Hostiles list if anybody is interested. I will also supply a converted version of the full hostiles list if you are brave enough to try it lol. Maybe in another week or so. I do not know how effective the shortened version will be as it will lack most individual addresses and concentrate on the larger ranges and the most important of the small ranges that 'I am aware of'. Edit: 17 hours later and the specific ip mentioned earlier has pinged me 26,000 times, now the 2nd largest pinger. 70.73. with 152,000. But then I have not been doing network searches which keeps some of the other ranges more quiet. |
| ||||
| See bottom of the first post on page 1.  There's an updated version released recently. The previous version had not been updated in 15 months. The TechNutopia Fullsize Hostiles List for BearShare and LimeWire, page 1 Alternatively, I'll repeat two of the download links: Download the Fullsize Hostiles List 2013 via MediaFire via SaberCat You have choice between an installer or just the hostiles file and instructions on where to place it. These files are in same folder as the Connection Fix installers at each of those sites. Last edited by Lord of the Rings; December 23rd, 2013 at 11:20 PM. Reason: Changed link from Hotfile to MediaFire after Hotfile closed down |
| ||||
| Quote:
199.127.249.95:38790 LimeSharePro/1.5.0 199.127.249.95:38229 morph500 199.127.249.241:20433 WinMX Music 199.127.253.17:40695 WinMX Music 199.127.253.17:36696 GTK-Gnutella 199.127.253.89:38982 WinMX Music 199.127.253.89:36865 morph500 199.127.253.89:46032 WinMX Music On another note, I have finally finished a shortened version of the Hostiles for LW 5. Two versions, I am referring to one as Light Security, and the other as Medium Security. They both have the main hosts listed. The Light one also lightens up on Japan a little, closer to the original full Hostiles blocks of Japan. Both seem to run fine with LPE in testing so far without any lag or other issues detected during long sessions. I will first package the LW and FW installers with installers for such lists, then post links to 'add them yourself' versions here. On a sadder note. I tried the BearShare Full Hostiles out with 3 versions of LW 4 and neither LW was able to connect and only whilst the hostiles file was within the folder. Not even the simplest of hints of trying to connect. Makes me wonder if it were really a myth the full-hostiles was compatible with LW 4. Unless the problem is related to my set-up, which is a possibility. Regardless, the newer LW blocklist versions will hopefully suffice for LW 4 users. For LW 4, I thus have 3 versions: light, medium and strong security. |
 |
| |
 LinkBacks (?)
LinkBacks (?)
LinkBack to this Thread: https://www.gnutellaforums.com/bearshare-open-discussion/53973-technutopia-fullsize-hostiles-list-bearshare-limewire.html | ||||
| Posted By | For | Type | Date | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 22nd, 2016 09:01 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 11th, 2014 10:48 AM | |
| Site Gnutella Forums | www.gnutellaforums.com | BoardReader | This thread | Refback | May 7th, 2014 04:33 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | December 18th, 2013 03:15 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | November 5th, 2013 02:07 AM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 03:15 PM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 03:39 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | July 14th, 2013 04:01 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | May 21st, 2013 12:24 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | May 4th, 2013 05:05 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | March 15th, 2013 11:11 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 24th, 2013 05:36 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | November 5th, 2012 12:37 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | October 8th, 2012 09:59 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 7th, 2012 04:05 AM | |
 Similar Threads
Similar Threads | ||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| The TechNutopia Fullsize Hostiles List for BearShare and LimeWire | AaronWalkhouse | Tips & Tricks | 18 | March 20th, 2009 09:45 PM |
| Hostiles File - I'm Lost | ADKR | General Windows Support | 7 | December 25th, 2007 08:03 PM |
| Is anybody having trouble connecting to www.technutopia.com? | AaronWalkhouse | Chat - Open Topics - The Lounge | 19 | August 6th, 2006 06:34 PM |
| The LimeWire Fullsize Hostiles List. | AaronWalkhouse | New Feature Requests | 1 | July 16th, 2005 06:03 PM |
| hostiles.txt in CVS tree | number_man | Gtk-Gnutella (Linux/Unix/Mac OSX/Windows) | 0 | May 22nd, 2004 07:58 AM |