
 |
| |||||||
| Register | FAQ | The Twelve Commandments | Members List | Calendar | Arcade | Find the Best VPN | Today's Posts | Search |
| BearShare Open Discussion Open topic discussion for BearShare users
Preview this popular software (BearShare Beta v5 "Download") |
 |
| | LinkBack | Thread Tools | Display Modes |
| ||||
| As an example of BOT's still around the network, using Phex I've highlighted some in the following GiF images. The GiF shows the finding in the hosts connection window, then after blocking the blocked hits count after an hour or two, then a few hours later and again a day later. Notice the ShareAza with the same address as the Phex's. Also two Phex's connected via the same port. After I removed all these hosts, more Phex's of same address but different ports than shown here connected briefly until I blocked the address. Also shown is a BOT identifying itself as LW4.16. Phex Connections window:  . . Phex Security window: . . Phex Security window:  |
| ||||
| An example of BOTs still around the network in 2017. Running BearShare without the hostiles file resulted in a notable number of BOTs connecting. Although I did sew some of these (the 4.12 Pro's) together over about an hour due to them only connecting briefly. Also some of these were downloading from me. Every host shown is a BOT. 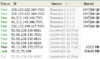 All those hosts are not what they appear to be, they give fake ID's. Here's a couple of examples from several years ago: seen via Phex and seen via BearShare The present version of BearShare Hostiles (Jan 2016) is somewhat out of date but will still do a good job of blocking out most BOTs. But unfortunately will also block out a heck of a lot of innocent hosts. Even my own dynamic address has changed to a different blocked range six or so occasions this year (no exaggeration.) I hope I'll be able to release an update over coming weeks or so. |
| ||||
| Instead of spending a life-time to attempt to update the Hostiles from Jan 8, 2016, a smaller version (used by LimeWire and WireShare) has been converted from CIDR to the Netmask format used by BearShare. Reasons: 1. The bulk of the original BearShare hostiles is out-of-date, with most of it having been added during the first decade of this century. 2. The internet landscape has changed dramatically over the past 10 years in most countries. New ISPs (internet service providers) have appeared, some larger ISPs have taken over multiple smaller ones. These ISPs have re-allocated many ip address ranges to other purposes such as from business or government to residential. A good example is a very large range that previously belonged to the UK government (pensions dept.) has been divided with UK gov using a half & the remainder split up and shared between residential use in UK, at least 3 European countries and Saudi Arabia. ie: ipv4 ranges have also been changed since last decade with some ranges now used by different countries. Other examples: 146.198.0.0/16, 146.200.0.0/16, 165.120.0.0/16 previously owned in USA now belong to two ISP’s in the UK. ISP's also lease or purchase ip ranges from other ISP's as they need. How many people in the world still have the same ip address to the one they used ten years ago! 3. Last decade probably over 80% of the world's internet addressing system (ip addresses) were Static (never changed.) Whereas these days probably well over 75% of the world's ip addresses are now dynamic (change from anywhere between daily to every couple of years depending on ISP policy applied. In my experience, there's highly dynamic and sticky dynamic; the latter might be based on either 3 or 6 week, 3 or 6 month, one or more years turnaround time; there's also a variable/random dynamic policy used by an ISP in Australia, Austria, Norway & Singapore & probably several others ~ these ip addresses might change from after a day (or a few times a day) up to over 6 months & the ipv4 address lifespan duration changes each time.) I'm not aware of any country that does not now use dynamic addressing for a percentage of residential purposes and that includes every continent and country large or small. 4. Question marks exist over many of the additions to the hostiles file in the first place. Last decade it was the default for most gnutella programs to immediately share downloaded files. Some people (myself included) might not check all files they downloaded for weeks or even months. I greatly suspect many additions to the hostiles file were not BOTs but accidental sharers of bad files. Do hosts accidentally sharing bad files 10+ years ago still deserve to be blocked? I doubt the hosts were really periodically re-checked and removal of hosts made on any consistent note (if at all.) It would have been far too difficult to re-check over half a million blocks representing many, many millions of individual hosts. Some of the logic (post #1 of this thread topic on page 1) about updating virus/malware scanners, etc. was barely applicable for those using MacOSX, not to mention an odd logic in any case. 5. Some organisations involved in spamming, attempted interruption or investigating the network last decade have since stopped, either replaced with new ones or never replaced. Edit 2018-04-29: I've personally found my own unique dynamic ip address within a range block on the hostiles more than a dozen occasions over the past 15 months and more than this over past 3 years despite removing the blocked range or part of it each time. I've also noticed with the old hostiles at least a couple of BearShare hosts would not have been able to connect to other BearShare hosts if using the original hostiles file. There's probably been at least a handful of such false-positive ('cry wolf') hostile blocks directly affecting BearShare hosts. Nothing wrong with the ip ranges these BearShare hosts are/were using in recent times. If there's doubt, the blocks remain. The newer hostiles is smaller but no less effective. The biggest plus is now you will be able to connect to more innocent hosts (faster connecting time) and find more files. The newer hostiles is sized around 29-30,000 hosts compared to the original hostiles of 2011 of over half a million or the 2016 version of 430,000. Regular BearShare users will find the program quite noticeably starts up much faster than previously as the hostiles is loaded (previously it could take 10 to 20 seconds depending on computer.) Whilst the full-Japanese hostiles version has been retained, it is definitely not recommended. Using this will definitely slow your connections to the gnutella network, and besides, you might also be losing out on finding files. They share both local & international content.  There is also a Super-Light hostiles option. This file only contains hostiles found over the past 5 or so years & have still been active hostiles over the past year (around 1,800.) I made some effort to avoid adding hostile hosts that change their addresses frequently. The Super-Light hostiles is 6% the size of the new but larger hostiles and around 0.3% the size of the BearShare hostiles of previous years. Although the BearShare hostiles update download links have been repeated a few times in this topic thread, I'll repeat them once more below: via SaberCat via MediaFire (ad-blocker advised) via 4Shared (need to be a member of this site to download & be extremely careful of pop-up windows such as fake Flash plug-in updates not belonging to Adobe website, fake virus messages, priority download or false download buttons. The genuine button is usually next to the Share button. Then choose Free download. sighs! I'm reluctant to use 4Shared these days but the download links have been the same since early this decade.) |
| ||||
| I periodically like to remind people about BOTs on the Gnutella network. I set-up Phex on a different OS to usual and recorded a few findings after 24 hours. Some of the same old BOTs still around and of course the port 27016 Spam-BOTs that show up with different addresses periodically. GTK-Gnutella has its own way of blocking BOTs. During the 2014-15 period I helped with the addition of ways to block three BOT types for WireShare. But for all other BOT variations and for all other LIME code based programs and including BearShare, the best way to block these hostile hosts is via using a hostiles security block list. Below is a few listings of BOTs seen at moments over a day. The first picture, a connection listing is from two snapshots taken one hour apart. The Phex security block window shows some of the BOT block rules I set-up and how many times they had been blocked within a 24 hour (or less) period. I've also shown a pic of a connection listing of PyGnutella from Jan 2012 using the same port as the other PyGnutella's still use now. The reason for the range blocks is because each range belongs to a particular company and in many cases the BOTs are dispersed across the range. (1)  . (2) . (2) 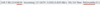 . (3) . (3) 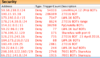 |
| ||||
| I want to apologise to those few persons who downloaded the BearShare Hostiles update over the past 48 hours. I forgot to test the files before deploying to the public. There was an error in two of the files that causes BearShare to delete the contents and replace it with a minimal outdated (2005) list with a file size of around 4 KB. This usually occurs within 5 to 10 seconds of the BearShare window showing up on screen during startup.  The installers have been updated to fix the problem (207.177.64.0/255.255.192.0 had a double //) You can either re-download the hostiles updater or re-install and fix the error yourself (within the db folder of the BearShare program folder.)  The super-light hostiles was unaffected. The file sizes should be over 800 KB each or over 60 KB for the super-light hostiles. Definitely not 4 KB which is a clear sign of an error in the file. There were also an extra two BOT addresses added in this fresh update compared to two days ago. |
 |
| |
 LinkBacks (?)
LinkBacks (?)
LinkBack to this Thread: https://www.gnutellaforums.com/bearshare-open-discussion/53973-technutopia-fullsize-hostiles-list-bearshare-limewire.html | ||||
| Posted By | For | Type | Date | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 22nd, 2016 08:01 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 11th, 2014 09:48 AM | |
| Site Gnutella Forums | www.gnutellaforums.com | BoardReader | This thread | Refback | May 7th, 2014 03:33 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | December 18th, 2013 02:15 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | November 5th, 2013 01:07 AM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 02:15 PM | |
| Bearshare pro 5 (download torrent) - TPB | This thread | Refback | August 16th, 2013 02:39 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | July 14th, 2013 03:01 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | May 21st, 2013 11:24 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | May 4th, 2013 04:05 AM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | March 15th, 2013 10:11 AM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | February 24th, 2013 04:36 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | November 4th, 2012 11:37 PM | |
| BearShare Pro-5.3.0 (download torrent) - TPB | This thread | Refback | October 8th, 2012 08:59 PM | |
| BearShare PRO 5.2.6.0 {Full Cracked Installer} (download torrent) - TPB | This thread | Refback | August 7th, 2012 03:05 AM | |
 Similar Threads
Similar Threads | ||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| The TechNutopia Fullsize Hostiles List for BearShare and LimeWire | AaronWalkhouse | Tips & Tricks | 18 | March 20th, 2009 08:45 PM |
| Hostiles File - I'm Lost | ADKR | General Windows Support | 7 | December 25th, 2007 07:03 PM |
| Is anybody having trouble connecting to www.technutopia.com? | AaronWalkhouse | Chat - Open Topics - The Lounge | 19 | August 6th, 2006 05:34 PM |
| The LimeWire Fullsize Hostiles List. | AaronWalkhouse | New Feature Requests | 1 | July 16th, 2005 05:03 PM |
| hostiles.txt in CVS tree | number_man | Gtk-Gnutella (Linux/Unix/Mac OSX/Windows) | 0 | May 22nd, 2004 06:58 AM |